The Iranian threat actor known as Tortoiseshell has been attributed to a new wave of watering hole attacks that are designed to deploy a malware dubbed IMAPLoader.
“IMAPLoader is a .NET malware that has the ability to fingerprint victim systems using native Windows utilities and acts as a downloader for further payloads,” the PwC Threat Intelligence said in a Wednesday analysis.
“It uses email as a [command-and-control] channel and is able to execute payloads extracted from email attachments and is executed via new service deployments.”
Active since at least 2018, Tortoiseshell has a history of using strategic website compromises as a ploy to facilitate the distribution of malware. Earlier this May, ClearSky linked the group to the breach of eight websites associated with shipping, logistics, and financial services companies in Israel.
The threat actor is aligned with the Islamic Revolutionary Guard Corps (IRGC) and is also tracked by the broader cybersecurity community under the names Crimson Sandstorm (previously Curium), Imperial Kitten, TA456, and Yellow Liderc.
The latest set of attacks between 2022 and 2023 entails embedding malicious JavaScript in compromised legitimate websites to gather more details about the visitors, including their location, device information, and time of visits.
These intrusions focused primarily on the maritime, shipping and logistics sectors in the Mediterranean, in some cases leading to the deployment of IMAPLoader as a follow-on payload should the victim be deemed a high-value target.
IMAPLoader is said to be a replacement to a Python-based IMAP implant Tortoiseshell previously used in late 2021 and early 2022, owing to the similarities in the functionality.
The malware acts as a downloader for next-stage payloads by querying hard-coded IMAP email accounts, specifically checking a mailbox folder misspelled as “Recive” to retrieve the executables from the message attachments.
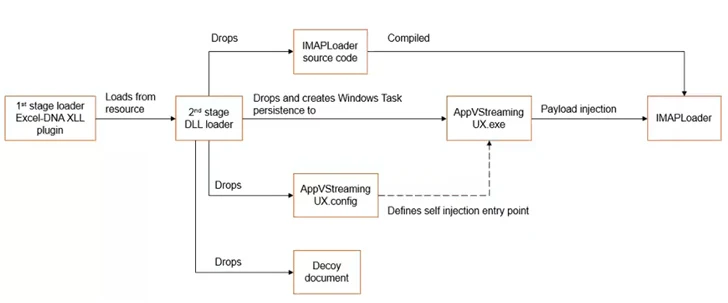
In an alternate attack chain, a Microsoft Excel decoy document is used as an initial vector to kick-start a multi-stage process to deliver and execute IMAPLoader, indicating that the threat actor is using a variety of tactics and techniques to realize its strategic goals.
PwC said it also discovered phishing sites created by Tortoiseshell, some of which are aimed at the travel and hospitality sectors within Europe, to conduct credential harvesting using fake Microsoft sign-in pages.
“This threat actor remains an active and persistent threat to many industries and countries, including the maritime, shipping, and logistics sectors within the Mediterranean; nuclear, aerospace, and defense industries in the U.S. and Europe; and IT managed service providers in the Middle East,” PwC said.