21 people have been arrested across the UK as part of a nationwide cyber crackdown targeting customers of WeLeakInfo[.]com, a now-defunct online service that had been previously selling access to data hacked from other websites.
The suspects used stolen personal credentials to commit further cyber and fraud offences, the NCA said.
Of the 21 arrested—all men aged between 18 and 38— nine have been detained on suspicion of Computer Misuse Act offences, nine for Fraud offences, and three are under investigation for both. NCA also seized over £41,000 in bitcoin from the arrested individuals.
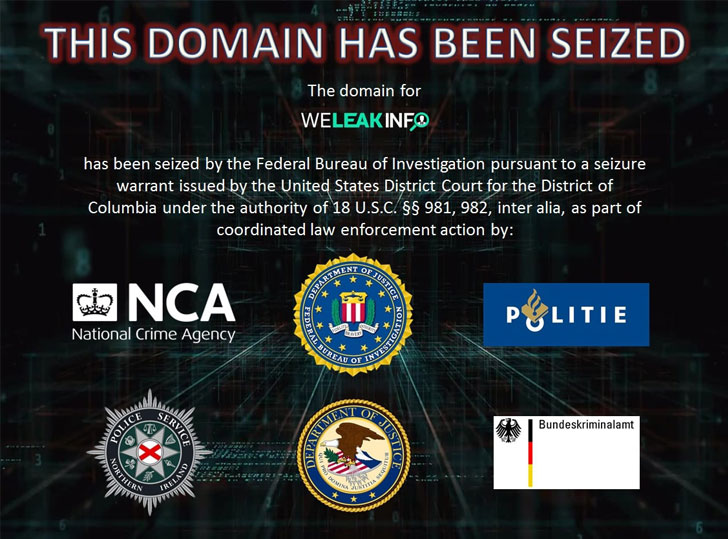
Earlier this January, the US Federal Bureau of Investigation (FBI), the UK National Crime Agency (NCA), the Netherlands National Police Corps, the German Bundeskriminalamt, and the Police Service of Northern Ireland jointly seized the domain of WeLeakInfo.com.
Launched in 2017, the service provided its users a search engine to access the personal information illegally obtained from over 10,000 data breaches and containing over 12 billion indexed stolen credentials, including, for example, names, email addresses, usernames, phone numbers, and passwords for online accounts.
On top of that, WeLeakInfo offered subscription plans, allowing unlimited searches and access to the results of these data breaches during the subscription period that lasted anywhere from one day ($2), one week ($7), one month ($25), or three months ($70).
The cheap subscriptions made the website accessible to even entry-level, apprentice-type hackers, letting them get hold of a huge cache of data for as little as $2 a day, and in turn, use those stolen passwords to mount credential stuffing attacks.
Following the domain’s seizure in January, two 22-year-old men, one in the Netherlands and another in Northern Ireland, were arrested in connection with running the site. WeLeakInfo’s Twitter handle has since gone quiet.
NCA said besides being customers of the website, some of the arrested men had also purchased other cybercrime tools such as remote access Trojans (RATs) and crypters, with three other subjects found to be in possession of indecent images of children.
“Cyber criminals rely on the fact that people duplicate passwords on multiple sites and data breaches create the opportunity for fraudsters to exploit that,” NCA’s Paul Creffield said. “Password hygiene is therefore extremely important.”