Cisco has patched a critical security vulnerability impacting its Enterprise Network Function Virtualization Infrastructure Software (NFVIS) that could be exploited by an attacker to take control of an affected system.
Tracked as CVE-2021-34746, the weakness has been rated 9.8 out of a maximum of 10 on the Common Vulnerability Scoring System (CVSS) and could allow a remote attacker to circumvent authentication and log in to a vulnerable device as an administrator.
The network equipment maker said it’s aware of a publicly available proof-of-concept (PoC) exploit code targeting the vulnerability, but added it’s not detected any successful weaponization attempts in the wild.
The issue is caused due to incomplete validation of user-supplied input that’s passed to an authentication script during the sign-in process, enabling an attacker to inject parameters into an authentication request. “A successful exploit could allow the attacker to bypass authentication and log in as an administrator to the affected device,” the company said in an advisory.
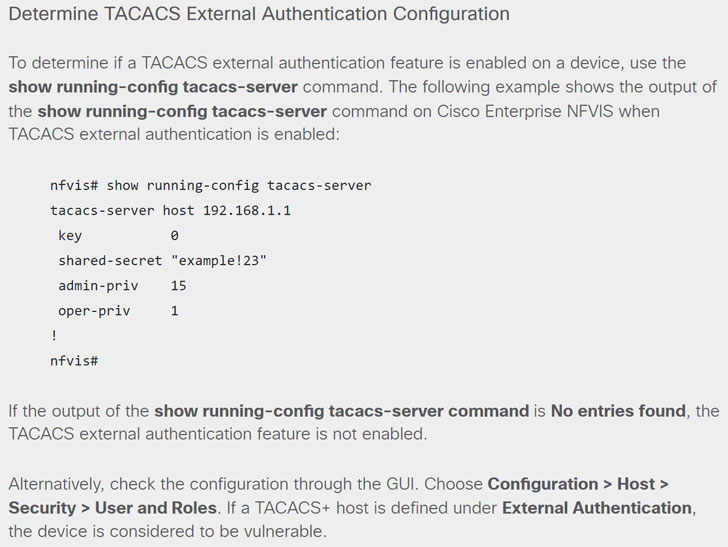
It’s worth pointing out that enterprise NFVIS deployments are impacted by this vulnerability only if TACACS external authentication method is configured on a targeted device, which can be determined by running the “show running-config tacacs-server” command. “If the output of the show running-config tacacs-server command is No entries found, the TACACS external authentication feature is not enabled,” the company noted.
The patches come a little over a week after Cisco rolled out updates to address a critical security vulnerability (CVE-2021-1577) affecting the Application Policy Infrastructure Controller (APIC) interface used in its Nexus 9000 Series Switches that could be potentially abused to read or write arbitrary files on a vulnerable system.
The company is also in the process of readying fixes for a zero-day bug (CVE-2021-1585) in its Adaptive Security Device Manager (ADSM) Launcher that could allow an unauthenticated, remote attacker to execute arbitrary code on a user’s operating system.