Cybersecurity researchers have disclosed details of a now-patched zero-day flaw in Google Cloud Platform (GCP) that could have enabled threat actors to conceal an unremovable, malicious application inside a victim’s Google account.
Dubbed GhostToken by Israeli cybersecurity startup Astrix Security, the shortcoming impacts all Google accounts, including enterprise-focused Workspace accounts. It was discovered and reported to Google on June 19, 2022. The company deployed a global-patch more than nine months later on April 7, 2023.
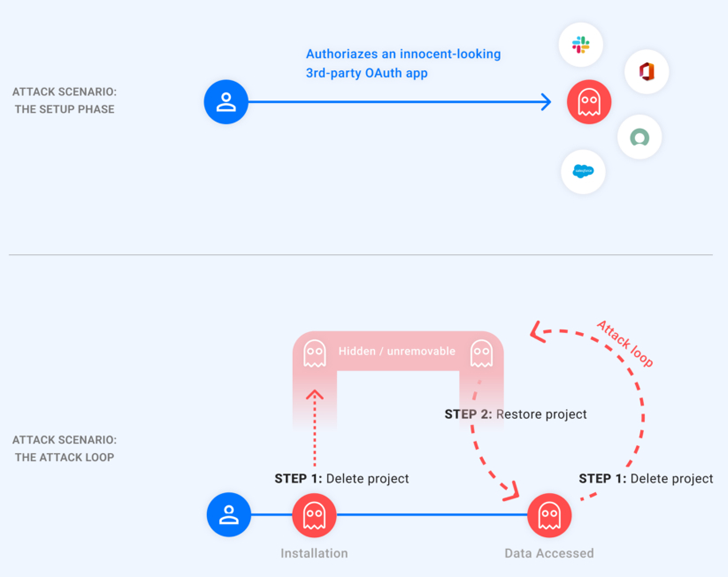
“The vulnerability […] allows attackers to gain permanent and unremovable access to a victim’s Google account by converting an already authorized third-party application into a malicious trojan app, leaving the victim’s personal data exposed forever,” Astrix said in a report.
In a nutshell, the flaw makes it possible for an attacker to hide their malicious app from a victim’s Google account application management page, thereby effectively preventing users from revoking its access.
This is achieved by deleting the GCP project associated with the authorized OAuth application, causing it to go in a “pending deletion” state. The threat actor, armed with this capability, could then unhide the rogue app by restoring the project and use the access token to obtain the victim’s data, and make it invisible again.
“In other words, the attacker holds a ‘ghost’ token to the victim’s account,” Astrix said.
The kind of data that can be accessed depends on the permissions granted to the app, which the adversaries can abuse to delete files from Google Drive, write emails on the victim’s behalf to perform social engineering attacks, track locations, and exfiltrate sensitive data from Google Calendar, Photos, and Drive.
“Victims may unknowingly authorize access to such malicious applications by installing a seemingly innocent app from the Google Marketplace or one of the many productivity tools available online,” Astrix added.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
“Once the malicious app has been authorized, an attacker exploiting the vulnerability can bypass Google’s “Apps with access to your account” management feature, which is the only place where Google users can view third-party apps connected to their account.”
Google’s patch addresses the problem by now displaying apps that are in a pending deletion state on the third-party access page, allowing users to revoke the permission granted to such apps.
The development comes as Google Cloud fixed a privilege escalation flaw in the Cloud Asset Inventory API dubbed Asset Key Thief that could be exploited to steal user-managed Service Account private keys and gain access to valuable data. The issue, which was discovered by SADA earlier this February, was patched by the tech giant on March 14, 2023.
The findings come a little over a month after cloud incident response firm Mitiga revealed that adversaries could take advantage of “insufficient” forensic visibility into GCP to exfiltrate sensitive data.