A significant number of victims in the consumer and enterprise sectors located across Australia, Japan, the U.S., and India have been affected by an evasive information-stealing malware called ViperSoftX.
ViperSoftX was first documented in 2020, with cybersecurity company Avast detailing a campaign in November 2022 that leveraged the malware to distribute a malicious Google Chrome extension capable of siphoning cryptocurrencies from wallet applications.
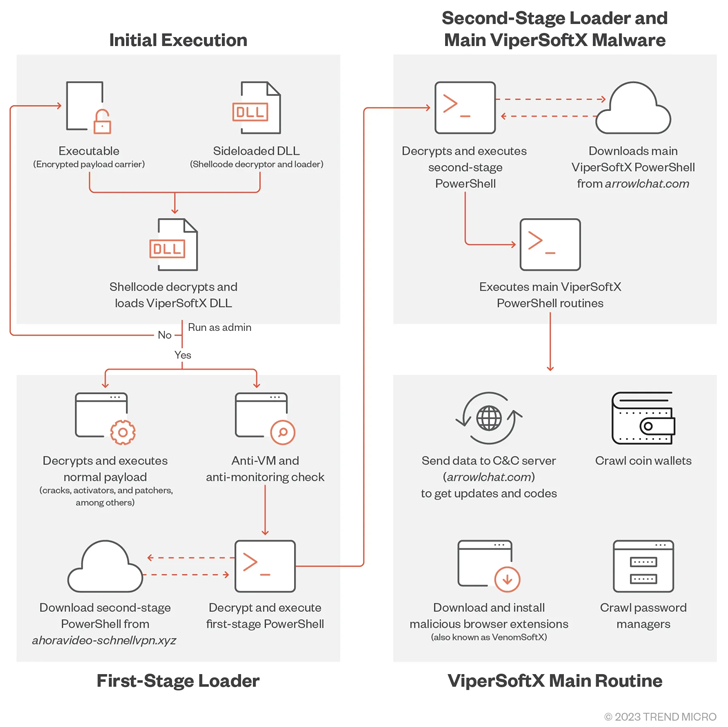
Now a new analysis from Trend Micro has revealed the malware’s adoption of “more sophisticated encryption and basic anti-analysis techniques, such as byte remapping and web browser communication blocking.”
The arrival vector of ViperSoftX is typically a software crack or a key generator (keygen), while also employing actual non-malicious software like multimedia editors and system cleaner apps as “carriers.”
One of the key steps performed by the malware before downloading a first-stage PowerShell loader is a series of anti-virtual machine, anti-monitoring, and anti-malware checks.
The loader then decrypts and executes a second-stage PowerShell script retrieved from a remote server, which then takes care of launching the main routine responsible for installing rogue browser extensions to exfiltrate passwords and crypto wallet data.
The primary command-and-control (C&C) servers used for the second stage download have been observed to change on a monthly basis, suggesting attempts on the part of the actor to sidestep detection.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
“It also uses some basic anti-C&C analyses by disallowing communications using web browsers,” Trend Micro researcher Don Ovid Ladores said, adding the updated version of ViperSoftX scans for the presence of KeePass 2 and 1Password password managers.
As mitigations, it’s advised that users download software only from official platforms and sources, and avoid downloading illegal software.
“The cybercriminals behind ViperSoftX are also skilled enough to execute a seamless chain for malware execution while staying under the radar of authorities by selecting one of the most effective methods for delivering malware to consumers,” Ovid Ladores added.