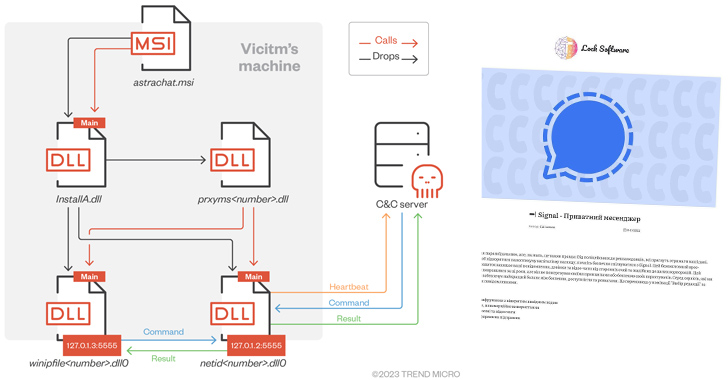
The threat actors behind RomCom RAT are leveraging a network of fake websites advertising rogue versions of popular software at least since July 2022 to infiltrate targets.
Cybersecurity firm Trend Micro is tracking the activity cluster under the name Void Rabisu, which is also known as Tropical Scorpius (Unit 42) and UNC2596 (Mandiant).
“These lure sites are most likely only meant for a small number of targets, thus making discovery and analysis more difficult,” security researchers Feike Hacquebord, Stephen Hilt, Fernando Merces, and Lord Alfred Remorin said.
Some of the impersonated apps spotted so far include AstraChat, Devolutions’ Remote Desktop Manager, Gimp, GoTo Meeting, KeePass, OpenAI ChatGPT, Signal, Veeam Backup & Replication, and WinDirStat.
RomCom RAT was first chronicled by Palo Alto Networks Unit 42 in August 2022, linking it to a financially motivated group deploying Cuba Ransomware (aka COLDDRAW). It’s worth noting that there is no evidence to suggest that the ransomware gang has any connection or affiliation with the Republic of Cuba.
The remote access trojan has since been used heavily in attacks targeting Ukrainian state bodies and military systems via spoofed versions of legitimate software. Other isolated targets have been located in the Americas and Asia.
Void Rabisu has also been observed abusing Google Ads to trick users into visiting the lure sites as part of narrowly targeted attacks, making it the latest addition in a long list of threat actors finding fresh avenues for gaining initial access into victims’ systems.
“RomCom used spear-phishing against a member of a European parliament in March 2022, but targeted a European defense company in October 2022 with a Google Ads advertisement that led to an intermediary landing site that would redirect to a RomCom lure site,” Trend Micro said.
This points to the adversary mixing its targeting methodology to encompass tactics associated with both cybercrime actors and nation-state groups.
The shift in RomCom RAT’s usage as a backdoor for targeted intrusions has been complemented by significant improvements to the malware that scales up the number of supported commands from 20 to 49, enabling it to exert total control over the compromised hosts.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
This also includes the ability to download additional payloads to take screenshots, grab crypto wallet data, siphon chat messages and FTP credentials, and use a browser password stealer dubbed StealDeal.
Another notable aspect of the attacks is the use of certificates to lend credibility to the malicious software installers, with samples signed by seemingly innocuous companies based in the U.S. and Canada.
“The line is blurring between cybercrime driven by financial gain and APT attacks motivated by geopolitics, espionage, disruption, and warfare,” the researchers said.
“Since the rise of Ransomware-as-a-Service (RaaS), cybercriminals are not using advanced tactics and targeted attacks that were previously thought to be the domain of APT actors. Inversely, tactics and techniques that were previously used by financially motivated actors are increasingly being used in attacks with geopolitical goals.”