A new data wiper malware called CryWiper has been found targeting Russian government agencies, including mayor’s offices and courts.
“Although it disguises itself as a ransomware and extorts money from the victim for ‘decrypting’ data, [it] does not actually encrypt, but purposefully destroys data in the affected system,” Kaspersky researchers Fedor Sinitsyn and Janis Zinchenko said in a write-up.
Additional details of the attacks were shared by the Russian-language news publication Izvestia. The intrusions have not been attributed to a specific adversarial group so far.
A C++-based malware, CryWiper is configured to establish persistence via a scheduled task and communicate with a command-and-control (C2) server to initiate the malicious activity.
Besides terminating processes related to database and email servers, the malware is equipped with capabilities to delete shadow copies of files and modify the Windows Registry to prevent RDP connections in a likely attempt to obstruct incident response efforts.
As the last step, the wiper corrupts all files with the exception of those with “.exe,” “.dll,” “lnk,” “.sys,” and “.msi” extensions, while also skipping specific directories, including C:Windows, Boot, and tmp, which could otherwise render the machine inoperable.
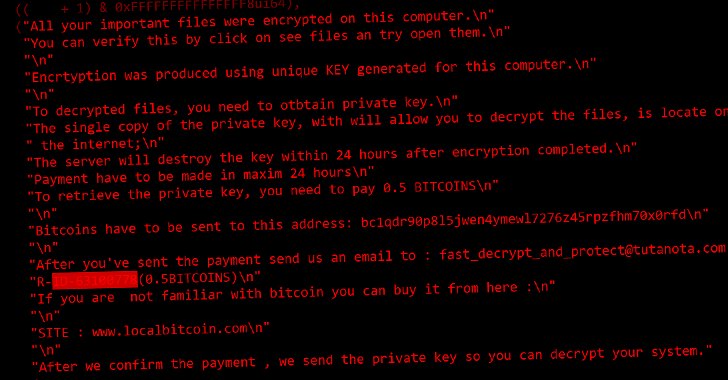
The files overwritten with garbage data are subsequently appended with an extension called “.CRY,” following which a ransom note is dropped to give the impression that it’s a ransomware program, urging the victim to pay 0.5 Bitcoin to recover access.
“The activity of CryWiper once again shows that the payment of the ransom does not guarantee the recovery of files,” the researchers said, stating the malware “deliberately destroys the contents of files.”
CryWiper is the second retaliatory wiper malware strain aimed at Russia after RURansom, a .NET-based wiper that was found targeting entities in the country earlier this March.
The ongoing conflict between Russia and Ukraine has involved the deployment of multiple wipers, with the latter hit with a wide range of malware such as WhisperGate, HermeticWiper, AcidRain, IsaacWiper, CaddyWiper, Industroyer2, and DoubleZero.
“Wipers can be effective regardless of the technical skills of the attacker, as even the simplest wiper can wreak havoc on affected systems,” Trellix researcher Max Kersten said in an analysis of destructive malware last month.
“The required time to create such a piece of malware is low, especially when compared to complex espionage backdoors and the often-accompanying vulnerabilities that are used. The return of investment need not be high in those cases, although it is unlikely that a few wipers are to wreak that much havoc in and of themselves.”